Quanterion developed and published the “Handbook of Software Reliability and Security Testing”, a comprehensive manual developed for the DoD’s Cyber Security and Information Systems Information Analysis Center (CSIAC).
The increasing complexity of modern systems, and systems-of-systems, is such that reliability considerations must extend beyond hardware, and include both software and human-machine interactions. This book specifically addresses software reliability and security, in terms of the reliability necessary to achieve the mission, the factors that influence the required reliability (e.g., customer expectations) and… Read More
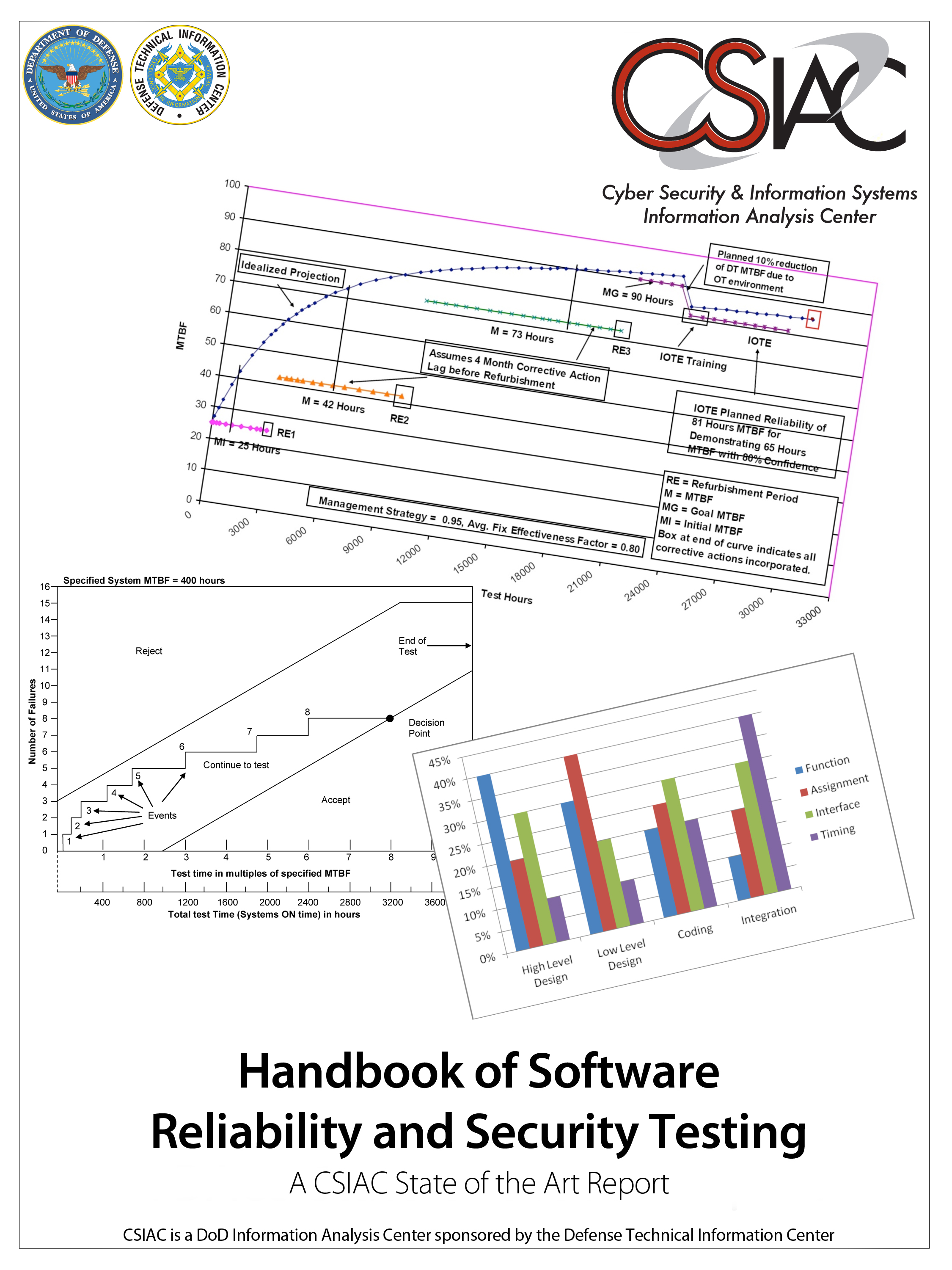
Handbook of Software Reliability & Security Testing
Cyber Security Metrics Workshop
Quanterion hosted a Cyber Security Metrics Workshop as part of its operation of the Cyber Security and Information Systems IAC (CSIAC). The one-day workshop reviewed current trends in policy, tools and techniques of interest to managers and Cyber Security professionals useful in measuring one’s cyber security vulnerability. It also provided an overview of the current state of understanding of what is presently available and will focus on what research needs to be done to develop robust and easy to use… Read More
SWMR
The Software Model Repository, an online database of software models, was initially developed by Quanterion during the operation of the DoD’s Data and Analysis Center for Software (DACS) and was transitioned to the Cyber Security and Information Systems Information Analysis Center (CSIAC). The objective of the SWMR effort is to collect, analyze and verify the existence and characteristics of software models for estimation, behavior, data, and object modeling to provide a centralized web-based repository that is accessible to researchers and… Read More
Embedded Phoenix Code Base
Under this effort, Quanterion is providing AFRL expertise in applying the Phoenix architecture concepts and base code, currently a mix of Java and C++, to the Cognitive Processor (CogChip) in a careful and fully-documented way, such that the resulting embedded C++ code base supports fully military compliant deployment and operational utility as a component of the Content and Context-aware Router (C2TR) effort. The C2TR is a medium-term effort to provide a robust capability for military networks to support advanced information… Read More
Advanced Geospatial Intelligence & Full Motion Video Exploitation
Quanterion is supporting AFRL in identifying new technologies, directing technical applications, performing demonstrations, conducting studies, analyzing and performing quick reaction demonstrations of concepts to determine the most effective and efficient method to exploit Measurement and Signature Intelligence (MASINT), Image Intelligence (IMINT), and Signals Intelligence (SIGINT) sources and methods. Quanterion is providing technology solutions and methods for collection management, exploitation of processed and stored data, dynamic cueing, situational awareness and assessment, and net-enabled approaches for interoperability to support operations.
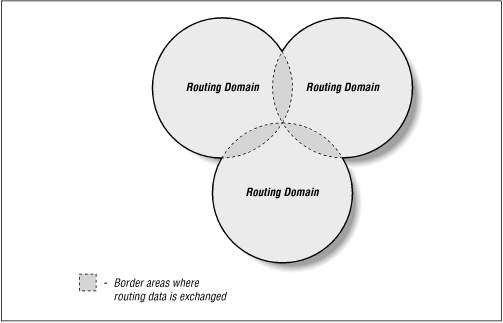
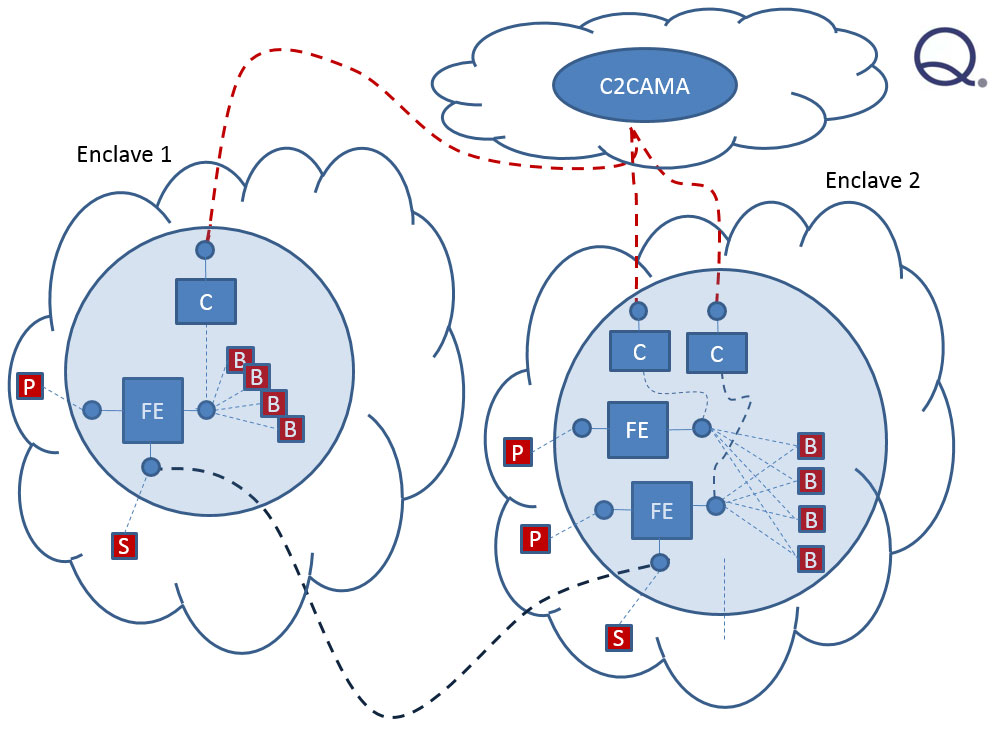
Trusted Protocol Routing Architecture
This effort supports the overall AFRL trusted protocol program by developing the architectural view more completely, even as some of the subtasks are executing in the research and development domain, and to compare and provide analysis on the evolution of the architecture through the beginning of the implementation phase. The objective of the effort under this task is to formulate an appropriate architecture sequence suitable for the spiral development of secure routing capability, while analyzing appropriate components of the current… Read More
Secure Routing Architecture Analysis
This effort supported Air Force Research Laboratory (AFRL) to design, architect and build a secure trusted router overlay for military networks based on the realization that many of the infrastructure components that the military depends on for movement of data between military enclaves are commercial end items that may not be configured or manufactured to meet the full qualifications of military mission objectives. Threats to unencumbered movement and assured delivery are the normal physical shortfalls, such as interrupted flow due… Read More